On your Mac, choose Apple menu System Preferences, click Security & Privacy, then click General. Open the General pane for me. Click the lock icon to unlock it, then enter an administrator name and password. Select the sources from which you'll allow software to be installed: App Store: Allows apps only from the Mac App Store. This is the most secure setting. Remove 'apple security alert' virus related Safari extensions: Open Safari browser, from the menu bar, select ' Safari ' and click ' Preferences.' In the preferences window, select ' Extensions ' and look for any recently-installed suspicious extensions. When located, click the ' Uninstall ' button next to it/them. Security is important—for you and for your files. Make sure your Mac stays protected with MacKeeper. It blocks malware, viruses, and spyware attacks to protect what matters most—your privacy.
How to remove AppleCare And Warranty from Mac?
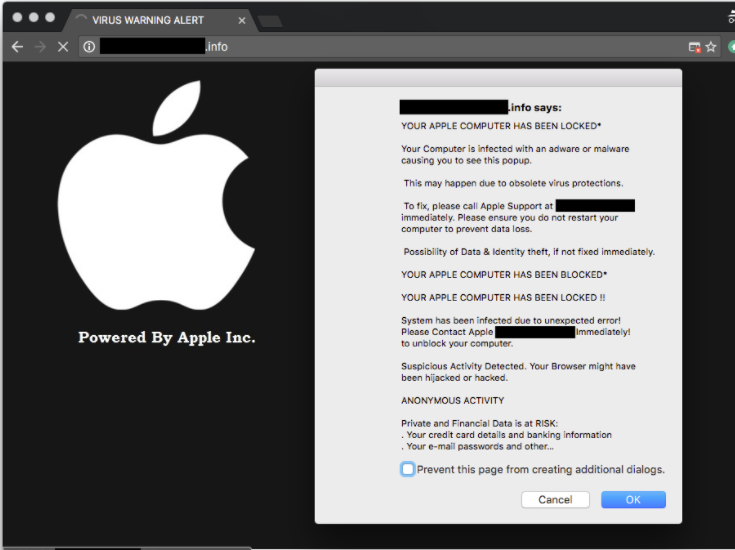
What is AppleCare And Warranty?
Displayed by a malicious website, 'AppleCare And Warranty' is a fake error message claiming that the system is infected. Research shows that users often visit this website inadvertently - they are redirected by potentially unwanted programs (PUPs) that typically infiltrate systems without permission. Be aware that these rogue programs are designed to misuse system resources, gather sensitive data, and deliver 'malvertising' ads (pop-ups, coupons, banners, etc.)
The 'AppleCare And Warranty' error targets the MacOS. It claims that the system is infected and, for this reason, users should immediately call '1-888-621-0834' to prevent further damage. After contacting 'certified technicians', users supposedly receive help removing malware and resolving other relating issues. In fact, 'AppleCare And Warranty' is a scam. This error is fake and it has nothing to do with Apple. Cyber criminals aim to extort money from unsuspecting users by encouraging them to pay for technical support that is not required. These people also aim to trick users into granting remote access to their computers. Once connected, they install malware and/or change system settings (e.g., users' passwords). Cyber criminals claim to 'detect' additional issues and offer help for an extra fee. For these reasons, you are advised to never call the aforementioned telephone number. 'AppleCare And Warranty' error can be removed by closing the web browser (preferably via Task Manager) or rebooting the system.
As mentioned above, potentially unwanted programs (and malicious websites) run unwanted processes (e.g., mine cryptocurrency) in the background. This misuse of resources significantly diminishes overall system performance. In addition, potentially unwanted programs record various user-system information that often includes personal data. Developers sell this information to third parties (potentially, cyber criminals). Therefore, the presence of virusThreat TypeMac malware, Mac virusSymptomsYour Mac became slower than normal, you see unwanted pop-up ads, you get redirected to shady websites.Distribution methodsDeceptive pop-up ads, free software installers (bundling), fake flash player installers, torrent file downloads.DamageInternet browsing tracking (potential privacy issues), displaying of unwanted ads, redirects to shady websites, loss of private information.Malware Removal (Mac)
To eliminate possible malware infections, scan your Mac with legitimate antivirus software. Our security researchers recommend using Combo Cleaner.
▼ Download Combo Cleaner for Mac
To use full-featured product, you have to purchase a license for Combo Cleaner. Limited three days free trial available.
'AppleCare And Warranty' shares many similarities with WARNING! MAC OS Is Infected, Apple Security Alert, Critical Security Warning!, and dozens of other fake errors. All state that the system is corrupted (e.g., missing files, infected, not protected, etc.), however, these claims are merely attempts to trick users into calling and paying for technical services that are not required. Research shows that potentially unwanted programs are very similar. By falsely claiming to enable 'useful functions', PUPs attempt to give the impression of legitimacy and trick users to install, however, their only purpose is to generate revenue for the developers. Rather than delivering any real value for regular users, PUPs risk users' privacy and browsing safety.
How did potentially unwanted programs install on my computer?
Some PUPs are known to have official download/promotion websites, however, in most cases, they are distributed using the aforementioned ads and via a deceptive marketing method called 'bundling'. Therefore, due to lack of knowledge and careless behavior by many users, PUPs often infiltrate systems without permission. Developers hide 'bundled' apps within various sections (e.g., the 'Custom/Advanced' options) of the download/installation processes. Furthermore, many users rush/skip steps and click dubious ads. In doing so, they expose their systems to risk of various infections and compromise their privacy.
How to avoid installation of potentially unwanted applications?
The key to computer safety is caution - pay close attention when browsing the Internet and downloading/installing software. Malicious ads appear genuine, but are distinguishable for their redirects - most lead to surveys, gambling, adult dating, pornography, etc. As mentioned above, they are often displayed by malicious apps. Therefore, if you encounter them, immediately remove all suspicious applications and browser extensions. Furthermore, carefully analyze each step (especially the 'Custom/Advanced' settings) of the download/installation processes and opt-out of all additionally-included programs. Note that third party download/installation tools are monetized using the 'bundling' method - they promote malicious apps and, thus, should never be used.
Text presented on the malicious website:
AppleCare and warranty Internet Security Damaged !!! Call Help Desk at 1-888-621-0834
Suspicious activation detected on, your IP address due to harmful virus installed in your computer. This virus can also damage the firewall security which can result in data loss or hard drive crash. Call immediately on the number provided, to rectify the issue.
We have disabled your computer to stop further damages to your computer. Do not restart your computer or shutdown. It may result in data loss. Please call us immediately to fix your security and to update the service agents of your computer software.
MAC Has Detected a Malicious Virus On Your System
Do Not Shutdown Or Restart Your Computer
Contact Our Certified MAC Technicians For Immediate Assistance.
Instant automatic Mac malware removal:Manual threat removal might be a lengthy and complicated process that requires advanced computer skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of Mac malware. Download it by clicking the button below:
▼ DOWNLOAD Combo Cleaner for MacBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. Limited three days free trial available.
Quick menu:
- STEP 1. Remove PUP related files and folders from OSX.
- STEP 2. Remove rogue extensions from Safari.
- STEP 3. Remove rogue add-ons from Google Chrome.
- STEP 4. Remove potentially unwanted plug-ins from Mozilla Firefox.
Video showing how to remove adware and browser hijackers from a Mac computer:
Potentially unwanted programs removal:
Remove PUP-related potentially unwanted applications from your 'Applications' folder:
Click the Finder icon. In the Finder window, select 'Applications'. In the applications folder, look for 'MPlayerX','NicePlayer', or other suspicious applications and drag them to the Trash. After removing the potentially unwanted application(s) that cause online ads, scan your Mac for any remaining unwanted components.
Combo Cleaner checks if your computer is infected with malware. To use full-featured product, you have to purchase a license for Combo Cleaner. Limited three days free trial available.
Remove 'applecare and warranty' virus related files and folders:
Click the Finder icon, from the menu bar. Choose Go, and click Go to Folder...
Check for adware-generated files in the /Library/LaunchAgents folder:
In the Go to Folder... bar, type: /Library/LaunchAgents
In the 'LaunchAgents' folder, look for any recently-added suspicious files and move them to the Trash. Examples of files generated by adware - 'installmac.AppRemoval.plist', 'myppes.download.plist', 'mykotlerino.ltvbit.plist', 'kuklorest.update.plist', etc. Adware commonly installs several files with the same string.
Check for adware generated files in the /Library/Application Support folder:
In the Go to Folder... bar, type: /Library/Application Support
In the 'Application Support' folder, look for any recently-added suspicious folders. For example, 'MplayerX' or 'NicePlayer', and move these folders to the Trash.
Check for adware-generated files in the ~/Library/LaunchAgents folder:
In the Go to Folder bar, type: ~/Library/LaunchAgents
In the 'LaunchAgents' folder, look for any recently-added suspicious files and move them to the Trash. Examples of files generated by adware - 'installmac.AppRemoval.plist', 'myppes.download.plist', 'mykotlerino.ltvbit.plist', 'kuklorest.update.plist', etc. Adware commonly installs several files with the same string.
Check for adware-generated files in the /Library/LaunchDaemons folder:
In the Go to Folder... bar, type: /Library/LaunchDaemons
In the 'LaunchDaemons' folder, look for recently-added suspicious files. For example 'com.aoudad.net-preferences.plist', 'com.myppes.net-preferences.plist', 'com.kuklorest.net-preferences.plist', 'com.avickUpd.plist', etc., and move them to the Trash.
Scan your Mac with Combo Cleaner:
If you have followed all the steps in the correct order you Mac should be clean of infections. To be sure your system is not infected run a scan with Combo Cleaner Antivirus. Download it HERE. After downloading the file double click combocleaner.dmg installer, in the opened window drag and drop Combo Cleaner icon on top of the Applications icon. Now open your launchpad and click on the Combo Cleaner icon. Wait until Combo Cleaner updates it's virus definition database and click 'Start Combo Scan' button.
Combo Cleaner will scan your Mac for malware infections. If the antivirus scan displays 'no threats found' - this means that you can continue with the removal guide, otherwise it's recommended to remove any found infections before continuing.
After removing files and folders generated by the adware, continue to remove rogue extensions from your Internet browsers.
'AppleCare and warranty' virus removal from Internet browsers:

Combo Cleaner will scan your Mac for malware infections. If the antivirus scan displays 'no threats found' - this means that you can continue with the removal guide, otherwise it's recommended to remove any found infections before continuing.
After removing files and folders generated by the adware, continue to remove rogue extensions from your Internet browsers.
'AppleCare and warranty' virus removal from Internet browsers:
Remove malicious extensions from Safari:
Remove 'applecare and warranty' virus related Safari extensions:
Open Safari browser, from the menu bar, select 'Safari' and click 'Preferences...'.
In the preferences window, select 'Extensions' and look for any recently-installed suspicious extensions. When located, click the 'Uninstall' button next to it/them. Note that you can safely uninstall all extensions from your Safari browser - none are crucial for normal browser operation.
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Safari.
Remove malicious plug-ins from Mozilla Firefox:
Remove 'applecare and warranty' virus related Mozilla Firefox add-ons:
Open your Mozilla Firefox browser. At the top right corner of the screen, click the 'Open Menu' (three horizontal lines) button. From the opened menu, choose 'Add-ons'.
Choose the 'Extensions' tab and look for any recently-installed suspicious add-ons. When located, click the 'Remove' button next to it/them. Note that you can safely uninstall all extensions from your Mozilla Firefox browser - none are crucial for normal browser operation.
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Mozilla Firefox.
Remove malicious extensions from Google Chrome:
Remove 'applecare and warranty' virus related Google Chrome add-ons:
Open Google Chrome and click the 'Chrome menu' (three horizontal lines) button located in the top-right corner of the browser window. From the drop-down menu, choose 'More Tools' and select 'Extensions'.
In the 'Extensions' window, look for any recently-installed suspicious add-ons. When located, click the 'Trash' button next to it/them. Note that you can safely uninstall all extensions from your Google Chrome browser - none are crucial for normal browser operation.
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Google Chrome.
It was once a widely held belief among Apple enthusiasts that macOS (or OSX as it was then known) was a far more secure system than its Windows or Linux counterparts. Malware outbreaks were rarely heard of, and most legacy AV solutions were known more for their high rate of false positives and greedy consumption of resources than they were for preventing any real adversaries. Asked 'do you really need antivirus software for macOS'? about the only reason Mac users would say 'yes' would be to catch Windows-based malware in email attachments. Why? In the words of this forum poster, as a public service to the unfortunate!
macOS Security By Design?
All that began to change from 2011 onwards, a fact reflected by Apple's increasing hardening of the OS. In every release of macOS since then, we've seen the introduction of more security technologies and a locking down of the system: Gatekeeper, codesigning, Xprotect, Malware Removal Tools and more. With the release of macOS Mojave this year, Apple once again introduced new security features in response to the evolving threatscape facing the platform, restricting Apple Events and hardening user data protections.
Apple, of course, should be commended for taking security seriously, something even they are aware that their users often do not. Apple says that macOS 'provides security by design' and
includes the key security technologies that an IT professional needs to protect corporate data and integrate within secure enterprise networking environments
The company are proud of their security posture, and are keen for customers to feel reassured that safety is a top concern:
macOS system security is designed so that both software and hardware are secure across all core components of every Mac. This architecture is central to security in macOS, and never gets in the way of device usability.
Fantastic. It's just what you want to hear from your OS vendor.
Except, it's all a bit of a myth.
As it turns out, malware can easily defeat macOS security protections. Let's take a quick look at the main reasons why relying solely on Apple's built-in protections is dangerous for your business.
Apple Virus Scan For Iphone
Application Security
You've probably got Gatekeeper turned on even if you don't know it. It comes enabled by default to allow you to download and run applications that are either from Apple's App Store or Identified Developers (in other words, developers who are part of Apple's Developer program).
Gatekeeper is great, except for one thing: it's only protecting one gate: downloads that come in through GUI apps like Safari, Mail and so on. But there's a few other gates that malware can use that Gatekeeper is blind to, like curl, ssh, and package managers such as brew. Download something through these channels, and Gatekeeper will never know. Note line 13 in this typical adware installer script, which bypasses Gatekeeper with ease:
You have likely heard of XProtect, and some may think that XProtect will plug the holes left open by Gatekeeper, but that's not the case. XProtect relies on Gatekeeper to tag downloads with a special attribute or 'quarantine bit' which effectively says to XProtect: 'be sure to check this against your malware signatures'. Without that attribute, XProtect doesn't kick in. What's worse, even software that is tagged with this special quarantine bit can be unquarantined by any other process without elevated permissions. In short, one piece of malware can let in any other piece of malware, too. Even if Apple have revoked a rogue Developer ID, such as occurs when malware strikes from the App Store, removing the quarantine bit will still allow that malware to run.
And then there's the paucity of XProtect's 'Yara' based rules. At last count, XProtect had less than 100 malware signatures. Although there was a minor bump in October of 2018, it hasn't had a significant update since March 2018.
There's also the transparency of XProtect's 'Yara' based rules. Any malware author can see exactly how Apple are detecting their binary and change it accordingly, so the rules can become invalid as soon as they are pushed out to users.
There's a third level of App Security built-in to macOS that is not so widely known called MRT, the Malware Removal Tool. According to Apple, in the event that malware should
make its way onto a Mac, macOS also includes technology to remediate infections
But there's two problems with Apple's malware removal tool which make malware unafraid of it: first, it's based on hard-coded paths, and most malware will use random or changing path names; second, it only runs once each boot.
By that time, a malware infection may have come and gone, taking your data with it, or encrypting it and leaving you a nice ransom note.
Access Control
Apple Security Scan Virus Protection
Central to access control on modern Macs is System Integrity Protection or 'SIP', aka 'rootless', which prevents malware from attacking system files. SIP is enabled by default, and it means that even the root user cannot modify or delete any files under its protection. In macOS Mojave, SIP can even be extended to 3rd party apps if they opt-in to the new hardened runtime.
SIP is an essential technology, but SIP bypasses are not unknown. It's also worth noting that if you have legacy AV software that simply whitelists everything in the /System/Library folder, you could be in for a shock, since not everything in there is actually protected by SIP. The following are all excluded from 'rootless' protection:
Another core aspect of access control is kernel security. As Apple have themselves noted, kernel security is essential to the security of the entire operating system. Unfortunately, their recognition of that is undermined by the fact that any unprivileged user can approve installing new kernel extensions. Combined with security holes that allow processes to simulate user clicks, therein lies an open door for malware. Apple have made several attempts to lock down simulated user clicking in the past, only for new 0day exploits to appear that have bypassed them.
If you're using a Mac that's enrolled in Apple's Device Enrollment Program, you will be familiar with MDM and Config profiles as a means of controlling access to applications, services and preferences. Malware authors are also aware of them, and have taken to slipping managed preferences onto user's machines to control and reset things like Safari preferences. Adware like Chill Tab and MyShopcoupon have been plaguing macOS users since mid-2017 through this same mechanism.
Apple Bugs
Arguably, these are becoming more common, or at least more widely publicised, as Apple pushes the limits of quality assurance in trying to keep up with its self-imposed annual update cycle. First, High Sierra and then Mojave introduced embarrassing bugs that could have given malware open season to infect and exploit macOS users.
Do You Really Need AV software on macOS?
We hope that the answer to this is self-evident by now. The built-in protections are 'nice to have', but they do not really address the complexity or sophistication of modern malware, especially when combined with Apple's determination to rush out a minimally-tested new version of the entire OS every 12 months.
If you have endpoints running macOS, you need a security solution that does more than scan a few static signatures and prevent downloads from one or two different sources. You need a solution that has defence in-depth: a modern Next-Gen solution like SentinelOne that uses machine learning to automate detection across your entire network, regardless of whether the endpoint is running macOS, Windows or Linux.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
